Implementing robust database auditing for Oracle Database has become essential for security and compliance. Organizations with comprehensive database auditing detect unauthorized access faster and reduce compliance preparation time significantly. According to IBM’s 2024 Cost of a Data Breach Report, data breach costs average $4.9 million in 2024, making thorough audit trail capabilities a business imperative.
Oracle Database provides sophisticated native auditing through Unified Auditing, but organizations often require advanced solutions to satisfy stringent compliance requirements. This guide explores Oracle’s built-in capabilities and demonstrates how DataSunrise enhances security monitoring with Zero-Touch Compliance Automation.
Understanding Oracle Database Auditing
Oracle Database auditing creates detailed records of database activities, user actions, and system events—capturing authentication attempts, data access patterns, SQL executions, and administrative operations for complete visibility.
Key security considerations include regulatory compliance (GDPR, HIPAA, PCI DSS, SOX), insider threat detection, data protection, forensic analysis, and operational intelligence. Oracle’s Unified Auditing provides a consolidated framework with enhanced performance and simplified administration.
Native Oracle Database Auditing Capabilities
Oracle Database includes powerful built-in auditing features for monitoring activities and maintaining security trails.
1. Unified Auditing Architecture
Oracle’s Unified Auditing consolidates audit logs into a single repository with superior performance.
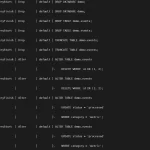
First, verify whether Unified Auditing is enabled:
-- Check if Unified Auditing is enabled
SELECT VALUE FROM V$OPTION WHERE PARAMETER = 'Unified Auditing';
If not enabled, relink the Oracle binary with uniaud_on and restart the database.
2. Creating Audit Policies
Create audit policies to define monitored activities:
-- Audit sensitive data access
CREATE AUDIT POLICY sensitive_data_access
ACTIONS
SELECT ON hr.employees,
UPDATE ON hr.employees,
EXECUTE ON hr.adjust_salary;
AUDIT POLICY sensitive_data_access;
-- Audit privileged users
CREATE AUDIT POLICY privileged_user_monitoring
ACTIONS ALL;
AUDIT POLICY privileged_user_monitoring BY sys, system;
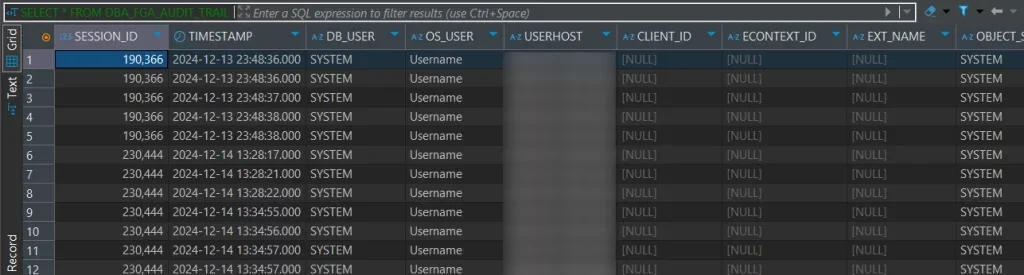
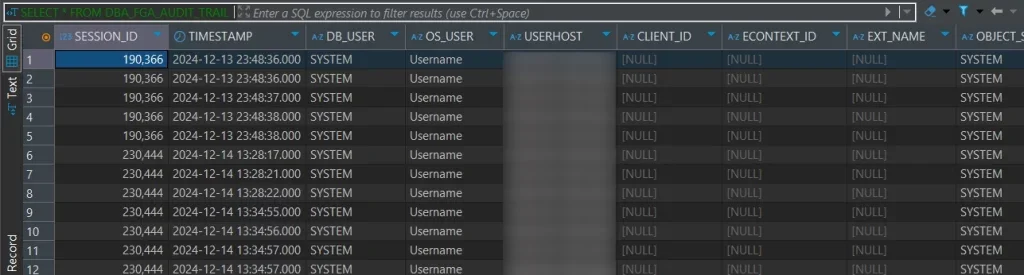
3. Testing Oracle Database Auditing
Execute sample operations to generate audit data:
-- Query sensitive data
SELECT employee_id, first_name, salary
FROM employees
WHERE salary > 10000;
-- Modify employee record
UPDATE employees
SET salary = salary * 1.05
WHERE employee_id = 145;
Limitations of Native Oracle Database Auditing
While Oracle’s native auditing provides essential functionality, organizations may encounter limitations:
| Native Feature | Key Limitation | Business Impact |
|---|---|---|
| Audit Policies | Manual configuration | Increased administrative overhead |
| Real-Time Alerting | Limited notifications | Delayed incident response |
| Cross-Database Visibility | No unified view | Fragmented monitoring |
| Sensitive Data Classification | Manual identification | Risk of missing critical data |
| Compliance Mapping | No automated integration | Time-consuming reporting |
Enhanced Oracle Database Auditing with DataSunrise
DataSunrise enhances Oracle auditing through Autonomous Compliance Orchestration and sophisticated analytics. Unlike basic logging, DataSunrise delivers comprehensive database activity monitoring with Zero-Touch Data Protection and No-Code Policy Automation.
Implementing DataSunrise for Oracle Database Auditing
1. Connect to Oracle Database Instance
Establish secure connection through the intuitive interface. DataSunrise supports all Oracle versions, RAC environments, and autonomous databases with SSL/TLS encryption.
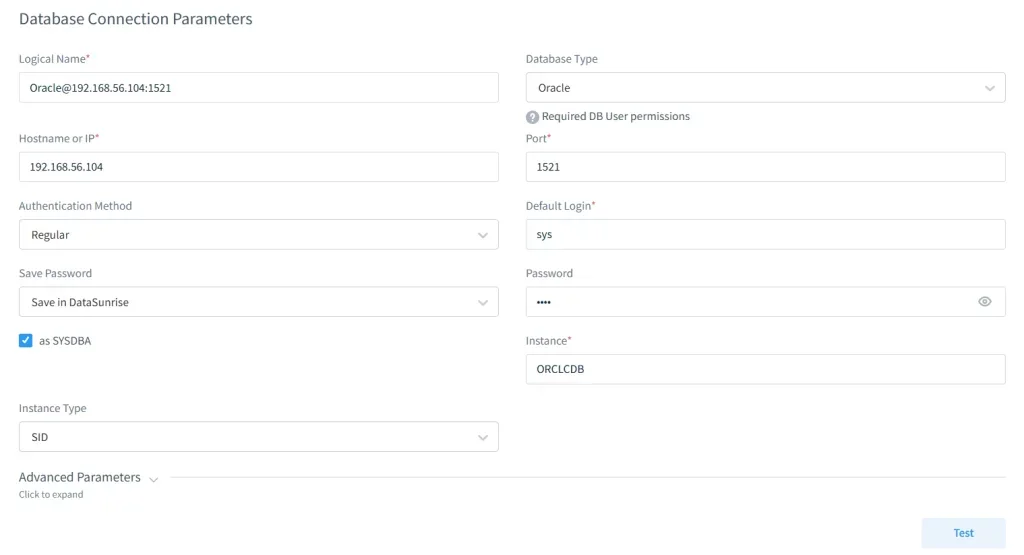
2. Configure Advanced Audit Rules
Create policies using No-Code Policy Automation with schema-level monitoring, object-level tracking, user-based policies, and query pattern analysis.
3. Review Comprehensive Audit Trails
Access detailed audit information through DataSunrise’s unified dashboard with real-time monitoring, advanced filtering, SQL reconstruction, and user behavior profiling.

Key Advantages of DataSunrise for Oracle Database
Auto-Discover & Classify: Automatically identify sensitive data using NLP and machine learning—ensuring comprehensive audit coverage without manual configuration.
No-Code Policy Automation: Create sophisticated policies without SQL scripting. Reduce implementation time from weeks to hours.
Real-Time Notifications: Receive immediate alerts through email, Slack, Teams, and webhooks for rapid incident response.
User Behavior Analysis: Establish baselines and detect anomalies using ML algorithms that adapt to changing patterns.
Automated Compliance Reporting: Generate pre-configured reports for GDPR, HIPAA, PCI DSS, SOX with audit-ready documentation.
Dynamic Data Masking: Protect sensitive data in real-time based on user roles while maintaining functionality.
Cross-Platform Visibility: Monitor Oracle alongside 40+ database platforms through unified console.
Best Practices for Oracle Database Audit Implementation
1. Strategic Audit Scope Definition
Identify sensitive data and apply intensive auditing to high-risk areas. Focus on privileged users and balance security policies with performance.
2. Performance Optimization
Avoid overly broad policies, use specific targeting, schedule intensive operations during off-peak hours, and implement regular audit storage management.
3. Compliance Framework Integration
Document audit coverage, create templates for regulatory frameworks, and generate automated compliance reports.
4. Security Operations Integration
Configure alerts with severity levels, integrate with SIEM platforms, and establish threat detection procedures.
5. Enhanced Implementation with DataSunrise
Deploy across all Oracle instances for consistent monitoring, leverage behavioral analytics, and enable cross-platform visibility.
Conclusion
As organizations rely on Oracle Database for critical operations, comprehensive auditing is essential for security and compliance. While Oracle’s Unified Auditing provides powerful functionality, enhanced solutions like DataSunrise deliver enterprise-grade security with Zero-Touch Data Protection, real-time monitoring, and Continuous Compliance Alignment across 40+ database platforms.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today